Substation Cybersecurity Explained
By William Conklin, Associate Editor

Substation Relay Protection Training
Our customized live online or in‑person group training can be delivered to your staff at your location.

- Live Online
- 12 hours Instructor-led
- Group Training Available
Download Our OSHA 3075 Fact Sheet – Understanding Electrical Hazards in the Workplace

- Learn the effects of electric current on the human body
- Understand OSHA safety standards and protective devices
- Discover essential lockout/tagout and grounding practices
Substation cybersecurity protects power grid infrastructure from cyber threats by securing communication networks, IEDs, and SCADA systems to ensure grid reliability and safety.
What is Substation Cybersecurity?
Substation cybersecurity safeguards digital power systems from cyberattacks. It ensures secure, stable, and resilient grid operation.
✅ Protects SCADA systems, RTUs, and IEDs from cyber threats
✅ Ensures data integrity and network communication security
✅ Supports compliance with NERC CIP and IEC 61850 standards
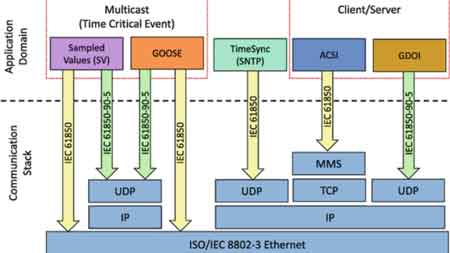
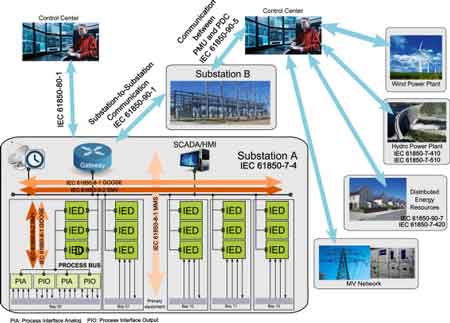
As power systems become increasingly digitized and connected, the importance of cybersecurity in substation and grid communications has grown exponentially. With the integration of intelligent electronic devices (IEDs), SCADA systems, and remote monitoring, modern substations are now part of a broader cyber-physical infrastructure. While these technologies enable real-time control and improved reliability, they also expose utilities to cyber threats that can disrupt critical services and damage essential assets. For a deeper understanding of how modern substation automation protocols intersect with cybersecurity strategies, take a look at our detailed resource on IEC 61850 Protocol, which outlines secure communication standards and device interoperability.
Ensuring the cybersecurity of substation networks is no longer optional—it's a core requirement for grid stability, national security, and compliance with regulatory standards such as NERC CIP (North American Electric Reliability Corporation Critical Infrastructure Protection). To understand how cybersecurity fits into the broader scope of grid infrastructure, visit our comprehensive guide on electrical substations, which covers design, functionality, and operational standards.
The Cyber Threat Landscape for Electric Utilities
Substations were once isolated, but the shift to remote access, IoT sensors, and cloud-connected platforms has expanded the attack surface dramatically. Today’s threats include malware, ransomware, insider threats, and state-sponsored attacks targeting the operational technology (OT) layer.
Sign Up for Electricity Forum’s Electrical Substations Newsletter
Stay informed with our FREE Electrical Substations Newsletter — get the latest news, breakthrough technologies, and expert insights, delivered straight to your inbox.
Because substations form the backbone of the transmission and distribution (T&D) network, any cyber incident can lead to blackouts, equipment failures, or cascading effects across the grid. Moreover, attackers often seek to exploit legacy devices, poor segmentation, or insecure remote connections to move laterally within the system.
NERC CIP Compliance: A Baseline for Protection
To address these growing risks, regulatory frameworks like NERC CIP have been developed to enforce a minimum standard of protection for critical infrastructure. NERC CIP governs the cybersecurity of bulk electric system assets across the U.S. and parts of Canada.
NERC CIP requires utilities to:
-
Identify and categorize critical cyber assets
-
Implement access control and authentication protocols
-
Maintain audit trails and perform log analysis
-
Conduct vulnerability assessments and incident response planning
-
Ensure physical and cyber perimeter security
Although NERC CIP provides a strong compliance foundation, it must be supplemented by real-time, adaptive defences to address evolving threats and zero-day vulnerabilities. Effective substation protection also depends on secure hardware—explore the importance of safe circuit breakers in maintaining both electrical and cyber safety.
Key Components of Substation Cybersecurity and Their Functions
| Component | Function | Cyber Threats Mitigated | Relevant Standards |
|---|---|---|---|
| Firewall & Network Segmentation | Isolates critical systems from external networks | Unauthorized access, malware spread | NERC CIP-005, IEC 62443 |
| Intrusion Detection System (IDS) | Monitors traffic for malicious activity | Zero-day exploits, brute force attacks | NIST SP 800-82, NERC CIP-007 |
| Authentication & Access Control | Verifies user identity and limits system access | Credential theft, insider threats | NERC CIP-004, ISO/IEC 27001 |
| Data Encryption (VPNs, TLS) | Protects data in transit between substations | Man-in-the-middle attacks, eavesdropping | NIST SP 800-52, IEC 62351 |
| Security Information and Event Management (SIEM) | Collects and analyzes logs for suspicious events | Advanced persistent threats (APT), anomalies | NERC CIP-007, NIST SP 800-137 |
| Patch Management System | Updates IEDs, RTUs, and HMI systems | Exploitation of known vulnerabilities | NERC CIP-010, IEC 61850 extensions |
Real-Time Threat Detection and Network Monitoring
Modern substations must go beyond static defences and implement real-time threat detection capabilities. This includes the deployment of intrusion detection systems (IDS), network security monitoring (NSM) tools, and behavioural analytics platforms tailored for industrial control systems (ICS).
These tools enable operators to:
-
Monitor communication patterns between IEDs, RTUs, and SCADA components
-
Detect anomalies such as unexpected protocol usage or lateral movement
-
Set automated alerts for known attack signatures or abnormal traffic volumes
-
Analyze network flows in segmented OT zones
Enhanced network visibility is critical, particularly when dealing with IEC 61850 protocols and other substation-specific communications that differ from traditional IT systems.
In addition, time-stamped logging, centralized SIEM integration, and forensic capabilities allow security teams to trace and respond to incidents rapidly, minimizing downtime and reducing impact. Since many substations rely on remote control systems, it’s important to consider RTU and HMI redundancy as part of your cybersecurity planning to prevent single points of failure.
Secure Remote Access: Balancing Convenience and Protection
With the growing need for remote substation management, secure access to field assets has become a top priority. However, enabling remote connections introduces significant risk if not implemented with strong controls.
Best practices for secure remote access include:
-
Multi-factor authentication (MFA) and role-based access control (RBAC)
-
Use of VPNs, jump servers, or zero trust access gateways
-
Enforcing least privilege principles and time-limited access
-
Logging and monitoring all session activity for compliance and incident review
-
Isolating IT and OT networks through firewall segmentation
As part of a broader zero trust architecture, these controls ensure that no user or device is inherently trusted, even if they are inside the perimeter. This significantly reduces the risk of lateral attacks and unauthorized access to critical systems.
The Role of Cyber Hygiene and Continuous Improvement
In addition to advanced tools, cyber hygiene practices form the foundation of a secure substation environment. Regular patching, software updates, network segmentation, and employee training are vital to preventing both intentional and accidental compromises.
Utilities should also develop a cybersecurity roadmap that includes:
-
Periodic penetration testing of OT and SCADA systems
-
Third-party vendor risk assessments
-
Supply chain integrity checks
-
Investment in cybersecurity skills and personnel
-
Incident simulation exercises and tabletop drills
By fostering a culture of cyber resilience, utilities can adapt more effectively to new threats and maintain trust in the reliability of the power grid. As substations expand in complexity, 3D substation design using AutoCAD offers a powerful way to visualize and integrate cybersecurity components during the planning phase.
FREE EF Electrical Training Catalog
Download our FREE Electrical Training Catalog and explore a full range of expert-led electrical training courses.

- Live online and in-person courses available
- Real-time instruction with Q&A from industry experts
- Flexible scheduling for your convenience
Conclusion
As substations evolve from isolated sites to intelligent, networked systems, cybersecurity in substation and grid communications has emerged as a top priority for utilities. Standards like NERC CIP provide a regulatory baseline, but true security requires active, layered defences including real-time threat detection, secure remote access, and network segmentation. With more substations incorporating sustainable practices, environmental substation design must now include strategies for both physical and cyber protection.
With the increasing complexity of the smart grid, utility operators must take a proactive approach to OT security, leveraging both technology and best practices to protect the integrity, availability, and confidentiality of their systems. In doing so, they safeguard not only infrastructure but the entire energy ecosystem that modern society depends on.
Related Articles